Project #1: Investigating the Value versus Privacy Cost of the Internet of Things
Faculty Mentors: Damla Turgut
Research: By applying relevant privacy frameworks from existing research literature (e.g., Privacy Calculus, Contextual Integrity, Association of Public-Safety Communications Officials, Internet Users’ Information Privacy Concerns, etc.), students will design their own experimental studies, collect data, and quantitatively analyze the data to understand the interplay between IoT data sharing practices and users’ privacy perceptions and outcomes. REU students will use a modified version of the Android operating system and a mobile application developed in the faculty mentor’s lab (i.e., PrivacyTrader by Dr. Turgut), to intercept the information flow between the Android devices and service providers. The students will conduct user studies that measure the actual information collected by the IoT devices, as well as the relative value users put on the services provided by the device versus the value of privacy lost through the disclosure of the information. The students will also perform de-anonymization research experiments to help test the value of anonymization measures and to develop better ones.
Project #2: IoT Device Vulnerabilities and Security
Faculty Mentors: Yier Jin and Shaojie Zhang
Research: IoT devices offer unparalleled functionality and convenience to both consumers and industry. As such, these devices are becoming more popular each day. However, as the number of connected devices increases, so do the security and privacy concerns. The unique properties of IoT devices and their design flow create a different breed of vulnerabilities unlike those found in general purpose computing systems. In contrast to general purpose systems, IoT developers frequently update the device’s firmware to provide more sophisticated functionality. Also, due to the shorter time-to-market (TTM), IoT devices often exhibit more debugging ports, such as testing interfaces and field update vectors, which make hardware-based attacks another threat. As such, the first topic in this project for undergraduate students is to investigate the security vulnerabilities on commercial IoT devices. Device hacking demos from the Dr. Jin and Dr. Zhang’s lab will be introduced, which students can use as inspiration, from both theoretical and practical aspects, to prove the ineffectiveness of current security protection methods on IoT devices. This research will further lead the students to investigate the fundamental reasons why the existing methods cannot protect IoT. Students may work on various directions which include: 1) Firmware Updating Schedule. The firmware updates happen rarely in the traditional embedded systems. However, for IoT devices, developers will update the firmware more frequently to install patches, and provide more sophisticated functionality. 2) Booting Process. The booting process becomes more vulnerable and leaves backdoors for attackers to exploit in IoT devices since security checks for booting process are rarely installed. The students will also be encouraged to perform independent studies on IoT security from the angles that are not covered from this project. This research is currently being supported by SCEEE grant 15-001: “Avalanche Effect in Cyber-Physical Systems Security Under Large-Scale Cyberattacks on Smart Devices” to which the students will contribute.
Project #3: Low Cost, Ultralow Power Sensor Design and Fabrication for IoT
Faculty Mentors: Hyoung Jin Cho
Figure 1: A packaged gas sensor

Research: In this research project, students will gain research experience in the design and fabrication of ultralow power, low cost chemiresistor-based sensors. Low power consumption and low cost are critical design considerations to IoT devices such as chemiresistor-based gas sensors that are widely used for safety monitoring in homes. These sensors require a fast response time, high selectivity and low detection limit. To achieve high sensitivity, traditional sensors require extra heating elements, adding to the cost and power consumption. This leads to the research challenge of designing and fabricating sensors based on nanoscale structures that achieve their performance targets without additional heating elements. In this project, the students will gain hands-on experience with the fabrication of a sensor using indium-doped tin oxide nanowires grown via the VLS (vapor-liquid-solid) method. The packaged device will be similar to one in Figure 2. With varying electrode configurations and processing conditions, students will study the dependence of sensor characteristics on design variables and processing conditions, compile and explain their findings in relation to the working principles of sensors.
Project #4: Energy-Efficient Computing Devices for IoT
Faculty Mentors: Mingjie Lin
Research: The students will perform and evaluate several key computing devices in an IoT environment. In particular, we let students to implement and experiment key components of a small synthesizable 32-bit RISC microprocessor. This embedded processor is one of the most critical computing devices in the modern IoT infrastructure. Our experimental system is currently running a live web server with an interrupt controller, UART, SRAM or DDR SDRAM controller, and Ethernet controller. This CPU executes all MIPS I(TM) user mode instructions except unaligned load and store operations. This “clean room” CPU core is implemented in VHDL with either a two or three-stage pipeline and running at 25 MHz on a Xilinx FPGA and also verified on an Altera FPGA, which now contains a bidirectional serial port, interrupt controller, and hardware timer. Students, under our supervision, will be responsible to add a DDR SDRAM controller, Ethernet MAC, or Flash interface. We will provide C and assembly code for its Real-Time Operating System, a fully preemptive RTOS supporting threads, semaphores, mutexes, message queues, timers, heaps, an interrupt manager, ANSI C library, single precision floating point library, TCP/IP protocol stack, and Web server. In short, we will provide a minimized yet complete computing IoT node to the participating students, and let them to add and modify it with the objective to understand how energy-efficient computing device is essential to the success of IoT.
Project #5: Generating Privacy and Security Threat Summary for Internet of Things
Faculty Mentors: Fei Liu
Research: This project’s primary research goal is to identify and summarize critical privacy and security threats of IoT technology through analyzing data from multiple news sources. Privacy and security are the top priorities. The project includes: (1) collect news articles from major U.S. news sources that are related to IoT privacy and security issues. The articles may include a) news releases for new IoT technologies and projects; b) media coverage of existing IoT technology vulnerabilities, e.g., media reports of IoT privacy and security issues, which have surfaced either through daily use or after malicious attacks. (2) identify and summarize privacy and security issues of the current and future IoT. Using the collected news data, students will learn to use state-of-the-art text analytics tools and investigate the emerging issues and perhaps manually summarize the cause, involved IoT technology, and consequences. Later, they will learn to use natural language processing, machine learning, and other data analytics tools to process the collected data and automatically generate text summary for the privacy and security threats. Students will perform research investigation using the extractive and compressive summarization techniques developed by Dr. Liu and colleagues to generate condensed text summary. Future study may include exploring language generation techniques to summarize the issues into text abstracts. Junior and senior undergrad students will be involved in data collection and gain hands-on experience on natural language processing research, and become aware of the critical issues related to the next-generation IoT technology. The summarized privacy and security issues may provide useful suggestions to the IoT technology developers and government agencies.
Project #6: Protection Scenarios to Preserve Privacy and Security within IoT Use Cases in Medical Simulation
Faculty Mentors: David Metcalf and Barbara Truman
Research: Organizations must comply with legal policies governing the privacy and security of devices and information involved in IoT use. This is especially true for health care providers dealing with laws protecting privacy such as HIPAA. Integrating effective practices for IoT security and privacy require new forms of analysis of monitoring. Some activities include identifying behaviors of users that hinder or promote the application of effective IoT principles. In health care settings, users bringing their own devices pose new opportunities and threats to health care provision. The goal of this project is to mitigate risk and inform effective practice to integrate IoT in a variety of health care use cases such as in a medical office, in-patient and out-patient hospital setting, surgical theatre, and military combat battlefield. The students will have the opportunity to conduct research for integrating secure and private IoT applications across a variety of use cases based on actual projects conducted in the Mixed Emerging Technology Integration Lab (METIL) at the UCF Institute for Simulation and Training. Medical simulation scenarios will be modeled using virtual environments based on real use cases that incorporate 3D visualization of human decisions and IoT interactions.
Project #7: Modeling Social Network Structures and their Dynamic Evolutions with User-Generated Data from IoT
Faculty Mentors: Guo-Jun Qi
Research: With user-generated data (UGD) from the IoT, such as GPS locations and their contacts, the involved undergraduates will develop new algorithms and systems to derive the social network structures and study how these structures evolve over time with continuously incoming streams of UGD. The blossom of IoT devices like smartphones and wearable devices, as well as the popularity of various apps on these devices, make it possible for us to study the social network structures underlying the uses of IoT and reason about the social and economic factors accounting for the formation, evolution and termination of these structures. This will deepen our understanding of many computational concepts and principles characterizing the users’ behaviors and intentions, thereby allowing companies to better serve these users. In this research, the involved students will have opportunity to sharpen their knowledge on graph theory, and perform research on deriving, tracking and predicting the latent social structures, such as communities and circles, over time. For example, the students will develop new models and algorithms to study how the social communities form and evolve by modeling and analyzing their GPS routings and communication patterns with their contacts. This research will reveal the dynamic interactions between the social communities that will evolve over time, splitting into smaller communities or merging into bigger ones. The students will base their modeling of the social structures on the UGD generated from IoT devices. Our previous projects have collected such UGD to build computational models for social network analysis. This will serve as a starting point for the students to start their research explorations. However, the undergraduates will need to tailor and clean the various genres of UGD to fit into the new research problems. The students will also design new mechanisms and scenarios to collect the UGD upon the IoT. For this purpose, this project will be coordinated with the other project(s), developing new apps to boost the users’ involvements as well as addressing their privacy concerns. The new scenarios will help reveal the hidden social network structures previously unknown to us from new dimensions of UGD measuring the users’ interactions.
Project #8: Internet of Hospital Things (IoHT): Communicating to Facilitate Healing
Faculty Mentors: Greg Welch and Yier Jin
Research: This project is related to the application of IoT principles to devices in a hospital. Today’s hospitals need to respond to patient needs, frequently under chaotic circumstances, while simultaneously keeping devices, drugs, and people meticulously organized to protect and prepare for patients. Medical devices, ranging from the mundane (e.g., a bed) to the complex (e.g., Doppler ultrasound devices, infusion pumps, and X-Ray machines), are surprisingly easily misplaced and difficult to monitor for preparedness (e.g., cleaning) and maintenance. We generally benefit from advances in devices and procedures, yet the advances are often accompanied by complexity that can increase the risk of human mistakes. While various real-time location tracking technologies are available commercially, most devices are typically isolated from each other, the hospital, and the patient. In the IoHT, defibrillators could be queried for their battery health and calibration status, infusion pumps could be remotely programmed for medication concentrations and flow rates, and patient-worn IoHT devices would estimate patient stress/pain and make medication adjustments. We seek to develop and test a proof-of-concept IoHT module that supports a common device interface protocol (e.g., IrDA) for one or more devices (e.g., a defibrillator or infusion pump), along with software implementing a general protocol and user interface that supports remote monitoring of device functions, perhaps including device location. We will test the modules using medical devices used at the College of Nursing for training purposes. We will work with technology specialists at Florida Hospital (FH) on specific device and design choices. (FH already tracks Stryker beds, infusion pumps, and even nurses.)
Project #9: Investigating User Benefits and Risks Associated with IoT use
Faculty Mentors: Pamela Wisniewski
Research: Users adopt wearable devices despite privacy and security concerns because the technology affords some level of value. Personal benefits may include enhanced self-awareness, positive behavior change, and cost savings. A number of such wearable IoT devices also allow end users to connect with other users to create synergistic social benefits, such as a sense of belonging, friendship, support, and even competition. For example, Fitbit users are able to track their steps to meet their personal fitness goals, but leveraging Fitbit’s social networking platform allows Fitbit users to also benchmark their progress with their friends, providing additional support and motivation. Many IoT devices have social plug-ins to external social platforms, such as Facebook, that allow users to disseminate their personal information to a broader network of others. It is important to understand users’ perceptions on why it may be valuable to share certain types of information so that the benefits of wearable IoT devices can be optimized. Yet, as these devices become more and more socially integrated, the privacy implications become even greater. Even when using wearable IoT devices for their intended purposes, users may share personal information accidentally or with unintentional, negative consequences. The goal of this project is to understand the social benefits and privacy risks faced by users when using devices for their intended purposes. Using qualitative techniques (e.g., semi-structured interviews, think-aloud cognitive walkthroughs with users of privacy management IoT interfaces, or web-based survey or diary studies), students will have the opportunity to conduct an in-depth, user-focused analysis to better understand the potential social benefits and privacy implications for IoT end users given the complex information sharing practices between wearable IoT devices and various social networking platforms. From this analysis, students will identify important emerging themes, suggest new features, and pinpoint potential opportunities for interface redesign that could enhance the benefits of IoT and wearable devices and/or minimize privacy risks for users.
Project #10: Innovative IoT Applications in Scientific Research and Consumer Market
Faculty Mentors: Shaojie Zhang and Yier Jin
Figure 2: A Sample Home Automation System Support by Smart Power Grid

Research: The development of IoT devices provides opportunities for innovative applications that would either significantly reduce the cost or achieve much higher performance. Supported by the REU Site, undergraduate students will have the chance to investigate new IoT applications to solve real-world problems. The research tasks will be divided into two main directions to help improve quality-of-life and to help preserve our natural environment. Towards the first direction, students will do research in improving the intelligence of home automation systems where different types of IoT devices will be included. Students will be encouraged to investigate and test various topologies for IoT device deployment and to design and test data communication protocols for efficient communication bandwidth optimization. Figure 1 shows a prototype where smart devices are leveraged to track and dynamically adjust the power consumption of a smart house. The research topics here include the data analysis method development, data communication, and smart house security. Meanwhile, towards the second direction, students will consider biology-related applications that currently rely on existing, less-connected embedded systems. As one leading example, students will work with graduate students from the PIs’ groups to develop a sophisticated and responsive bio-acoustic system for ecology research. The students will begin by gaining an understanding of the IoT devices, field recording challenges, and recognition algorithms through building a passive acoustic recording system. Next, the students will develop an active prototype with high computation power so that the developed system can recognize and extract bioacoustics signals from background noise.
Project #11: Security and Privacy of the Communication Channels among IoT Devices
Faculty Mentors: Cliff Zou and Damla Turgut
Figure 3: Dual channel validation to defend against fake access point attack
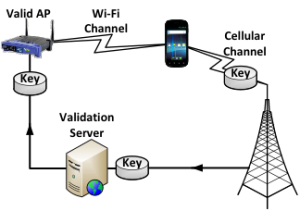
Research: One major reason why IoT devices become increasingly popular is that they enable users to remotely control other IoT devices, or remotely obtain valuable information. Thus the data communication channel between IoT devices and data collectors, or between IoT devices and the Internet, is the critical component for all IoT applications. However, because of the limited computing, storage or battery resources of most IoT devices, and because of the inherent insecurity of wireless communication channels (WiFi, ZigBee, Bluetooth, etc.), the security and privacy of IoT communication channels is a major concern for users and could slow down the success deployment of IoT applications. In this project, we will educate students with practical skills and cutting-edge research techniques on security issues associated with IoT device communication channels, especially WiFi, since it is the dominant communication mechanism for most IoT devices. In Dr. Zou’s lab, several easy-to-deploy prototypes have been developed to conduct and defend against fake WiFi Access Point attack (see Figure 3), Evil Twin attack, disassociation attack, and parallel on-line password dictionary attack. Students will have hands-on experience in setting up these prototypes, learning how to initiate those well-known WiFi attacks and more importantly, how to defend IoT devices against those attacks accordingly. By learning and having hands-on experience in related research work, the students will be guided to conduct their own research in proposing and brainstorming research ideas on defending against attacks in current and future IoT systems. Different IoT devices have very distinctive data-link layer traffic patterns. Even though WiFi traffic of most IoT devices could be encrypted, the encryption happens on the network layer or higher. Thus by eavesdropping WiFi traffic, attackers can figure out what IoT devices (even brand names) a home or a hotspot has, which poses a serious privacy concern for consumers. In this project, students will first learn how to conduct research on using suitable statistical data analysis tools to fingerprint IoT devices, and learn how to conduct MAC address randomization, and propose new mechanisms, to defend against this fingerprinting attack.

